
Case Study: A Leading NGO in Hong Kong
Case Study: Enhancing Data Security and Preventing
Leakage to Protect Vulnerable Communities for a Leading NGO in Hong Kong

Client: A Leading NGO in Hong Kong
Solution: Implementing IBM Guardium Data Encryption and Curtain e-Locker for End-to-End Encryption and Secure Access Control.
Client Profile:
Our client is a prominent NGO in Hong Kong, who manages a substantial volume of sensitive personal data pertaining to individuals receiving aid, financial contributors, employees, and program participants. Ensuring the secure handling and protection of this information is a critical operational priority, essential for maintaining public trust and fulfilling their mission of serving vulnerable communities.
The Challenges:
The client experienced a data leakage incident, highlighting vulnerabilities in their data security practices. This incident underscored the critical need for a comprehensive solution to protect sensitive data from unauthorized access and exfiltration, safeguarding the privacy and well-being of the individuals and communities they support. The client needed to ensure compliance with data privacy regulations and, most importantly, maintain the trust of their stakeholders and the vulnerable populations they serve.
The Solution:
To address the client’s data security challenges, OptimaTech implemented an end-to-end data security solution combining Curtain e-locker DLP (e-locker) and IBM Guardium Data Encryption (IBM GDE). e-locker provided granular access control and activity monitoring for classified data within the organization, while IBM GDE ensured comprehensive encryption of all classified data at rest and in transit, with an additional layer of access control. This synergistic approach enabled seamless user workflows while significantly mitigating the risk of unauthorized data exposure and leakage.
OptimaTech’s solutions encompassed the following key elements:
Enhanced Data Control with Curtain e-Locker:
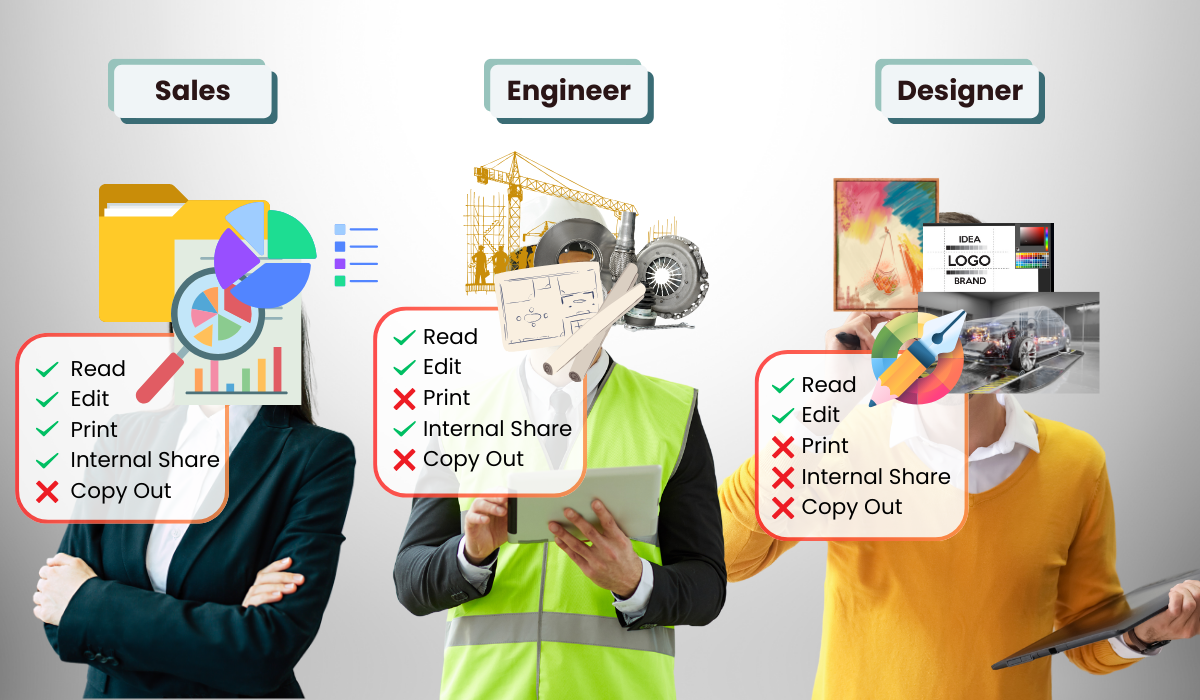
- Granular User Control Over File Permissions: Enabling the client to define precise access permissions based on user roles and needs, like saving, copying and pasting, sending files externally, taking screenshots, printing, editing, sharing internally, or setting it as read-only. Ensuring Least Privilege Principle are well deployed to enhance data security.
- Online / Offline Protection: Ensuring consistent data security regardless of network connectivity, with policies enforced both online and offline.
- Screen Watermarking: Implementing screen watermarks to deter visual data capture via screenshots or photographs, adding a powerful visual deterrent.
- Comprehensive File Activity Logging: Providing detailed audit trails of all file access and activities, enabling thorough monitoring and investigation of potential security incidents.
End-to-End Encryption with IBM GDE:
- At Rest and In Transit Encryption: IBM GDE was deployed to encrypt sensitive data both at rest and in transit. This ensures that even if data is accessed by unauthorized individuals, it remains unreadable without the proper decryption keys.
- Fine-Grained Access Control: Real-time data access control limited to need-to-know basis, determined by user/group roles. Based on user/group access levels and defined policies, IBM GDE returns queried data in clear text, encrypted form, or denies access.
- Ransomware Protection: IBM GDE blocks ransomware access to read or write protected files during attack attempts.
The Result:
The client has expressed strong satisfaction with OptimaTech’s solution and the resulting improvements in their data security posture. The implementation of Curtain e-Locker and IBM Guardium has yielded the following key benefits:
- Drastically Reduced Data Leakage Risk: This solution significantly minimizes the risk of future data leakage incidents, protecting the sensitive information of vulnerable communities.
- Enhanced Data Security, Compliance, and Governance: End-to-end encryption and refined data security handling significantly enhance the client’s data security posture, ensuring compliance with relevant data privacy regulations and strengthening overall data governance. Curtain e-locker’s features, including restricted printing, copying, and screen captures, combined with detailed activity logging, provide a comprehensive defence against both internal and external data leakage risks.
- Reinforced Trust with Vulnerable Communities and Stakeholders: By demonstrating a strong commitment to data security and protecting the privacy of those they serve, the client has reinforced trust among its stakeholders, including donors, beneficiaries, partners, and, most importantly, the vulnerable communities who rely on their services.
- Future Data Protection Expansion: Building upon the success of this implementation, the client is now considering extending the solution to protect other application data and Microsoft 365 data, demonstrating a commitment to a holistic security strategy.

Feel Interested? Contact Us For Details.
